Why OnyxOS Exists
Solana moves fast. But speed without privacy creates vulnerability. OnyxOS prioritizes privacy to protect your digital assets and transactions.
The Problem
- •Hidden approvals drain wallets silently
- •Metadata leaks expose transaction patterns
- •Routing fingerprints track your activity
- •Authority abuse goes undetected
- •Phishing attacks bypass user awareness
The Gap
- •Wallets focus on custody, not privacy
- •Scanners only react after damage is done
- •Privacy tools operate in isolation
- •No unified defense architecture exists
- •Users forced to patch together solutions
The Solution
- ✓Full operational privacy layer
- ✓Six integrated defense modules
- ✓AI-powered autonomous protection
- ✓Real-time threat correlation
- ✓Unified defense graph architecture
How OnyxOS Works
Not just tools. A complete operating system for privacy. Six integrated modules working as one unified defense.
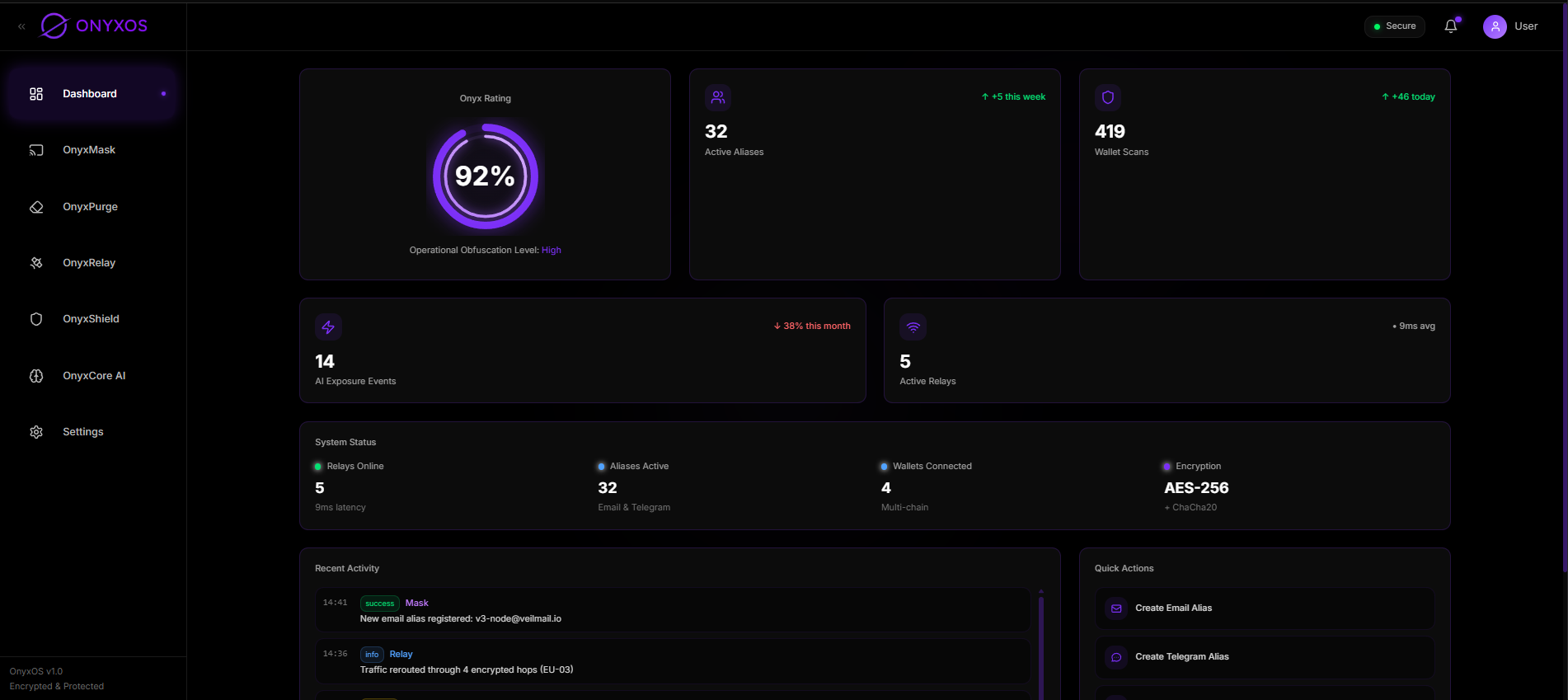
Dashboard
Operational cockpit
Low visibility
Unified control panel for all privacy layers
OnyxMask
Identity protection layer
Phishing & tracking
Isolates your real identity with governed aliases
OnyxPurge
Exposure control
Historical vulnerabilities
Cleans metadata and revokes dangerous approvals
OnyxRelay
Encrypted routing
Transaction fingerprinting
Routes through encrypted relays with rotation
OnyxShield
Real-time defense
Malicious signatures
Blocks exploits before transaction broadcast
OnyxCore AI
Adaptive intelligence
Unknown threats
Correlates signals and auto-responds to attacks
OS Architecture View
All modules communicate through OnyxCore AI for unified threat correlation
The Privacy Modules
Each module is a specialized privacy layer. Together, they form an impenetrable defense system.
OnyxMask
Identity Isolation Protocol
Your real identity never touches the chain. OnyxMask creates governed aliases that act as your public face while keeping your actual wallet address completely isolated.
Key Capabilities:
OnyxPurge
Exposure Cleanup Engine
Remove traces of past vulnerabilities. OnyxPurge scans your entire transaction history, identifies dangerous approvals, revokes permissions, and cleans metadata leaks.
Key Capabilities:
OnyxRelay
Encrypted Transaction Routing
Your transactions never reveal your location or patterns. OnyxRelay routes all activity through encrypted relay nodes with automatic rotation and latency monitoring.
Key Capabilities:
OnyxShield
Real-Time Signature Defense
Block malicious transactions before they execute. OnyxShield analyzes every signature request in real-time, checking against known exploits and permission abuse patterns.
Key Capabilities:
OnyxCore AI
Autonomous Defense Intelligence
The brain of the entire system. OnyxCore AI correlates signals across all modules, learns attack patterns, predicts threats, and autonomously responds to protect you.
Key Capabilities:
One OS. One Defense Graph.
The difference between isolated tools and a unified operating system is intelligence. OnyxOS doesn't just run modules—it orchestrates them.
Signal Flow
Every module feeds data into the defense graph. OnyxCore AI processes signals in real-time, building a complete threat picture that no isolated tool could see.
AI Correlation
The AI doesn't just analyze—it correlates. A suspicious relay pattern + metadata leak + permission change = high-confidence threat. Automated response triggered.
Defense Playbooks
Pre-programmed response sequences execute autonomously. No manual intervention. The system identifies, classifies, and neutralizes threats before they reach you.
- • Scanner detects threat after damage done
- • Wallet approval shows technical jargon
- • No connection between privacy events
- • Manual intervention required constantly
- • Reactive privacy posture
- ✓ Shield blocks threat before execution
- ✓ Dashboard shows plain-English risk summary
- ✓ AI correlates signals across all modules
- ✓ Autonomous responses protect automatically
- ✓ Proactive defense architecture
Where OnyxOS Stands Apart
Not all privacy solutions are created equal. Here's how OnyxOS compares to typical alternatives.
| Capability | OnyxOS | Typical Wallets | Typical Tools | Basic Privacy |
|---|---|---|---|---|
| Alias Privacy | ||||
| Permission Hardening | ||||
| Real-Time Threat Defense | ||||
| Metadata Cleaning | ||||
| Encrypted Routing | ||||
| Autonomous AI Responses | ||||
| Unified Dashboard | ||||
| Multi-Layer Defense |
> OnyxOS is the only solution with integrated, AI-powered, multi-layer defense
Become Part of the OnyxOS Network
Buy $ONYX tokens to unlock exclusive launch features, early access to the dApp, and become part of the Solana security revolution. Join the network that's redefining blockchain protection.
Privacy, Trust, Compatibility
Critical questions about how OnyxOS protects you without compromising control.